SHA1:
e2eb0b0c87b81d68b3f3f9675d3fda7a7bf8ba27
0004194f6ef57fe77fd23734a897e74fda56ebb0
393504cbfb30995b79378acea39b00bdda9deec7
37c2f95c3be60ba021c5e96cc02d278c55377656
8f9b50530d74a93582af54cc60faa412e6513b32
88a95ea5a37bf1bc56780327f639dc7806cea9bf
0004194f6ef57fe77fd23734a897e74fda56ebb0 (obfuscated modification detected as Android.ZBot.2.origin)
dc7b430bc5bb002c8bc8312050d2063d4e9e935d (obfuscated modification detected as Android.ZBot.3.origin)
A banking Trojan for Android mobile devices intended to steal money from users’ bank accounts. Masquerading as a benign program, it can be downloaded once a user visits fraudulent or hacked websites, or another malicious application can download it to a device.
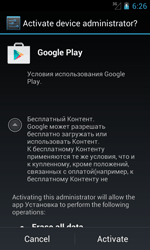
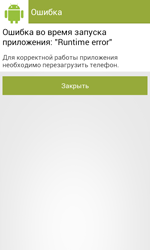
Once launched for the first time, Android.ZBot.1.origin tries to access administrator privileges and displays an error message urging the user to reboot the system. Then the Trojan removes its icon from the home screen.
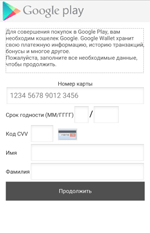
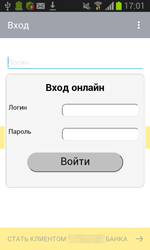
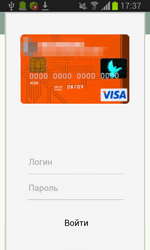
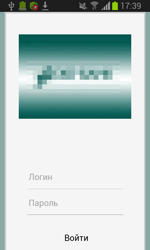
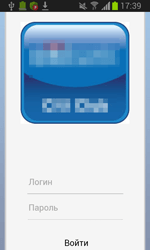
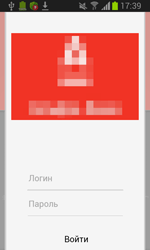
If the user refuses to grant the necessary privileges, Android.ZBot.1.origin attempts to steal the information on their bank card showing a bogus dialog simulating the input form of the legitimate Google Play application. The same dialog can be displayed in a period of time after the installation.
In order to be launched automatically after the compromised gadget is turned on, Android.ZBot.1.origin, using OnBootReceiver, monitors the following system events:
- android.intent.action.BOOT_COMPLETED—signals that the system is booted
- android.intent.action.QUICKBOOT_POWERON—signals that the device is rebooted in the Fast Boot mode and not in the usual mode.
Once the Trojan takes over control, it launches the UpdateService malicious service that tracks user's activity (android.intent.action.SCREEN_OFF, android.intent.action.SCREEN_ON), and, using AsyncTask, activates asynchronous tasks to connect to the server. In particular, it helps Android.ZBot.1.origin send the data on a compromised device to the command and control server and receive instructions in JSON (Java Script Object Notation). Besides, the server also gets the confidential information entered by the user as well as the information on the Trojan activity and its operation errors.
Upon a command from cybercriminals, Android.ZBot.1.origin can execute the following actions:
- Send an SMS with a specific text to a specified number
- Make a phone call
- Send text messages to all user’s contacts
- Intercept incoming SMS messages
- Track the current GPS coordinates
- Display a special dialog on top of a specified application
Once a compromised device is registered on the server, the Trojan receives the command to check the user’s bank account. If it detects availability of funds, it automatically transfers the specific sum of money to cybercriminals’ bank accounts. What is more, the malicious program intercepts and automatically processes all the incoming text messages with transactions verification codes from banks. As a result, the victim finds out about the theft not right after the crime is committed but some time later.
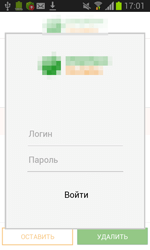
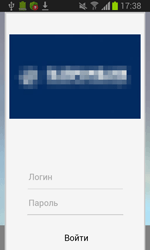
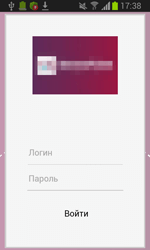
To display specially created dialogs, the server sends instructions to the Trojan that specify the applications on top of which a phishing message is to be shown. After that, Android.ZBot.1.origin identifies if these applications are on the device. If the Trojan finds a match, it periodically begins to check whether the corresponding application is running. Once such application is launched, the banking Trojan connects to the command and control server and downloads HTML code that, with the help of WebView, is displayed as a bogus dialog. Such fake dialogs often imitate authorization forms of online banking applications. If the victim of phishing tries to get rid of the shown message by tapping “Back”, Android.ZBot.1.origin will redirect the user to the home screen creating an illusion that this prompt really belongs to the corresponding legitimate application.
Some malicious features of Android.ZBot.1.origin (for example, sending text messages) are implemented in a separate Linux library named libandroid-v7-support.so that is stored inside of the Trojan’s program package and designed to protect the Trojan from anti-virus detection.
The base address of the Android.ZBot.1.origin server is stored in a special database named SQLite. However, it can be changed upon the cybercriminals’ command. By default, different Trojan’s modifications have their own addresses of command and control servers, so the compromised gadgets can create independent botnets.
Although such modifications of Android.ZBot.1.origin as Android.ZBot.2.origin and Android.ZBot.3.origin possess the same features as the original malicious program, their code is obfuscated (encrypted) in order to complicate the detection procedure.