- Packer: absent
- Compilation dates:
- 30.08.2020 18:02:53 (loader ccL100U.dll)
- 30.08.2020 18:01:38 (payload)
- SHA1 hashes:
- 14a652b5b9d71171224541ce2b950cf55da38190 (loader ccL100U.dll)
- f76ae6ee508cf22f52b8533d704667a1893860d9 (payload)
Description
A backdoor written in C and C++ and designed to run on 32- and 64-bit Microsoft Windows operating systems. Its main purpose is to provide a communication channel with the C&C server through DNS requests and facilitate unauthorized control over the infected computer. It consists of a malicious loader (a .DLL library), and the main module operating in RAM. Its code has multiple overlaps with the Cotx backdoor.
Operating routine
The malware is a DNS backdoor. C&C server communication occurs by reading the TXT records of subdomains formed in a certain way.
Loader module
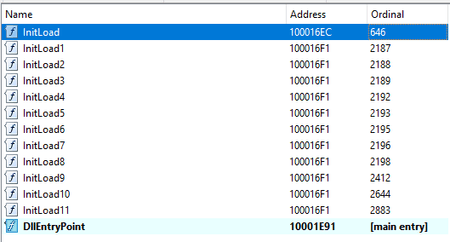
The original name in the export table is Stager.dll. The library has a number of exported functions.
With that, most of the functions do not perform any actions. The only working function is InitLoad, where the backdoor is launched. The same function is called from DllMain.
The backdoor unpacks the payload from its resources. It is located in the DAT resource compressed through RtlCompressBuffer виде. In the unpacked main module, the loader searches for the CQKUZXadCXS string, which is a plug for the configuration. After the string is found, the loader replaces it with the current configuration. In the analyzed sample, this string is AB1d3d3MS5kb3RvbWF0ZXIuY2x1Yjsw.
Next, the %WINDIR%\\System32\\dllhost.exe process is launched, where the main module is then injected. If the third character in the configuration is 0, both the executable file of the process in the context of which the loader operates and the file of the loader itself are deleted.
The main module operation
The main module is written in C++, with extensive use of the STL library.
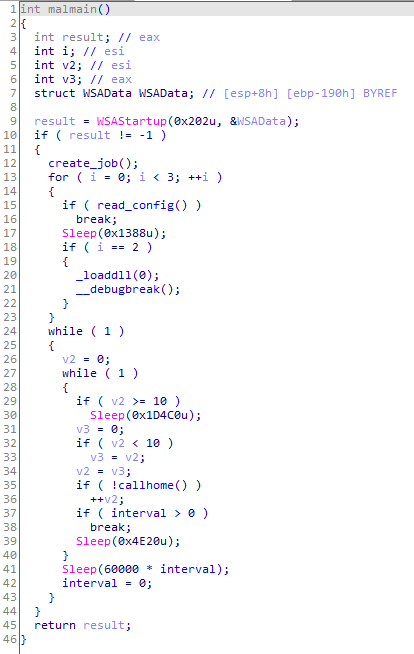
At the beginning, the backdoor verifies the embedded configuration that was earlier replaced by the loader. If the first two characters do not match AB, it considers the configuration to be absent, so it stops running. Otherwise, it decodes the configuration from Base64, starting from the 4th character: www1.dotomater.club;0.
The configuration format is simple and represents a domain of the C&C server and the IP address of the DNS server, which are separated by a semicolon. If the DNS server address is not specified or specified as null, the backdoor uses the DNS servers used by the infected computer.
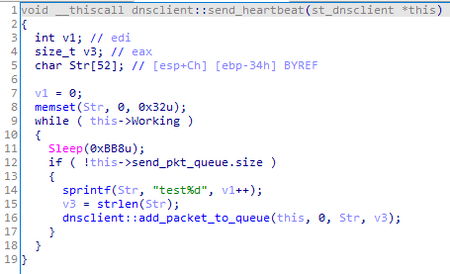
Next, the backdoor creates several threads. The first is used to send heartbeat packets.
In response, the C&C server sends the heartbeat%d string where %d is the same number from the packet sent by the bot.
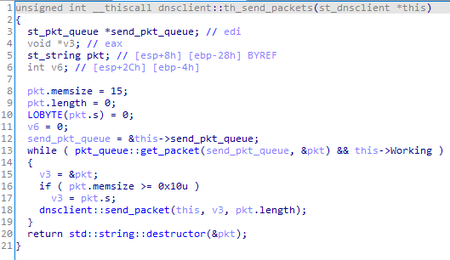
The second thread is used to parse the packets queue and send them to the C&C server.
After that, it transmits the information about the infected system:
sprintf(Str, "%s;%s;%s;%d;%s", szCompName, szUserName, szOSVer, isx64, szCurDateTime);
Next, the backdoor enters the cycle of receiving and processing commands from the C&C server.
| Command code | Command description |
|---|---|
| 1 | Set bot ID |
| 2 | Run the command shell and redirect the I/O to the pipes |
| 3 | Execute the command in the previously launched shell (command No.2) |
| 4 | Get information about the disk or directory listing |
| 6 | Send file to the C&C server |
| 7 | Copy a file |
| 8 | Delete a file |
| 9 | Get information about the file size |
| 10 | Save file to the specified path |
| 11 | Change the interval of C&C server communication |
| 13 | Self-deletion |
C&C server communication protocol
From the data sent to the C&C server the following structure is initially formed:
#pragma pack(push, 1)
struct st_packet
{
_BYTE magic; // 0x65
_WORD botid;
_DWORD pktid;
_BYTE data[];
};
#pragma pack(pop)
- botid initially has the 0 value, but it changes upon the C&C server command, containing opcode == 1, which is sent as a response to the information about the infected system;
- pktid has the initial value 0, but it changes upon receiving each packet from the C&C server;
- data contains the packet data, including command ID.
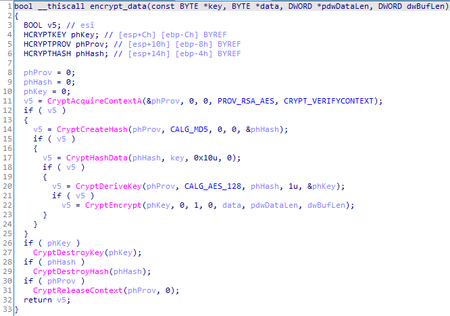
The received packet is encrypted with the following function:
The dadadadadadadada string is sent into this function as a key.
The received encrypted data is coded with Base64. From the encrypted data the subdomain name for the domain, listed in the configuration, is formed. With that, if the length of the encoded data exceeds 62 symbols, the dot is added after each 62nd symbol.
Next, the DNS request to receive TXT records of the formed domain is made.
The response from the C&C server is decrypted the same way. First, it is decoded from Base64, followed by decryption with the dadadadadadadada key. The resulting data is:
#pragma pack(push, 1)
struct st_recv_packet
{
_BYTE magic; // 0x65
_DWORD pktid;
_BYTE opcode;
_BYTE data[];
};
#pragma pack(pop)