- Packer: absent
- Compilation date: 07.03.2019 07:04:48
- SHA1 hash: fc698eb0d7d6948605a7e5ba6708752b691a3fec
Description
Trojan.Mirage.12 is a multi-component backdoor trojan written in C++ with the use of Active Template Library (ATL) and designed for Windows 32- and 64-bit operating systems. It is used to facilitate unauthorized control over infected computers and enabling access to information stored on them. The trojan is a COM server that operates in RAM within the system process.
Operating routine
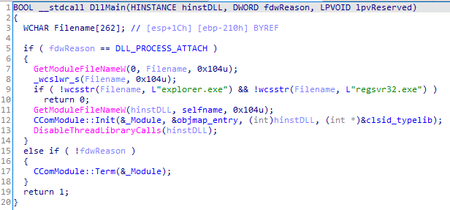
The trojan only operates if it is loaded into a process named explorer.exe or regsvr32.exe. This is due to the specifics of the sample’s operation: the trojan is registered in the system via regsvr32.exe, and its execution takes place in the context of explorer.exe.
When running through regsvr32 (with the key /i or without keys), the DllRegisterServer function exported by the trojan is called, which is responsible for registering its COM interface in the system:
[<HKLM>\Software\Classes\Server.ServerMain.1] '' = 'ServerMain Class'
[<HKLM>\Software\Classes\Server.ServerMain.1\CLSID] '' = '{D8956119-6E66-43BD-AAA5-231F94859EE6}'
[<HKLM>\Software\Classes\Server.ServerMain] '' = 'ServerMain Class'
[<HKLM>\Software\Classes\Server.ServerMain\CLSID] '' = '{D8956119-6E66-43BD-AAA5-231F94859EE6}'
[<HKLM>\Software\Classes\Server.ServerMain\CurVer] '' = 'Server.ServerMain.1'
[<HKLM>\Software\Classes\CLSID\{D8956119-6E66-43BD-AAA5-231F94859EE6}] '' = 'ServerMain Class'
[<HKLM>\Software\Classes\CLSID\{D8956119-6E66-43BD-AAA5-231F94859EE6}\ProgID] '' = 'Server.ServerMain.1'
[<HKLM>\Software\Classes\CLSID\{D8956119-6E66-43BD-AAA5-231F94859EE6}\VersionIndependentProgID] '' = 'Server.ServerMain'
[<HKLM>\Software\Classes\CLSID\{D8956119-6E66-43BD-AAA5-231F94859EE6}\InprocServer32] '' = ''
[<HKLM>\Software\Classes\CLSID\{D8956119-6E66-43BD-AAA5-231F94859EE6}\InprocServer32] 'ThreadingModel' = 'Apartment'
[<HKLM>\Software\Classes\CLSID\{D8956119-6E66-43BD-AAA5-231F94859EE6}\TypeLib] '' = '{1CAE5CEB-54C5-49E3-B195-4A76DD1A7C21}'
[<HKLM>\Software\Classes\TypeLib\{1CAE5CEB-54C5-49E3-B195-4A76DD1A7C21}\1.0] '' = 'Server 1.0 Type Library'
[<HKLM>\Software\Classes\TypeLib\{1CAE5CEB-54C5-49E3-B195-4A76DD1A7C21}\1.0\FLAGS] '' = '0'
[<HKLM>\Software\Classes\TypeLib\{1CAE5CEB-54C5-49E3-B195-4A76DD1A7C21}\1.0\0\win32] '' = ''
[<HKLM>\Software\Classes\TypeLib\{1CAE5CEB-54C5-49E3-B195-4A76DD1A7C21}\1.0\HELPDIR] '' = ''
[<HKLM>\Software\Classes\Interface\{CFDA1C1C-DB4B-431C-88A1-2C799A80A4BB}] '' = 'IServerMain'
[<HKLM>\Software\Classes\Interface\{CFDA1C1C-DB4B-431C-88A1-2C799A80A4BB}\ProxyStubClsid] '' = '{00020424-0000-0000-C000-000000000046}'
[<HKLM>\Software\Classes\Interface\{CFDA1C1C-DB4B-431C-88A1-2C799A80A4BB}\ProxyStubClsid32] '' = '{00020424-0000-0000-C000-000000000046}'
[<HKLM>\Software\Classes\Interface\{CFDA1C1C-DB4B-431C-88A1-2C799A80A4BB}\TypeLib] '' = '{1CAE5CEB-54C5-49E3-B195-4A76DD1A7C21}'
[<HKLM>\Software\Classes\Interface\{CFDA1C1C-DB4B-431C-88A1-2C799A80A4BB}\TypeLib] 'Version' = '1.0'
where <path> is the path to trojan’s file and <homedir> is its home directory.
The trojan enables its autorun also via regsvr32: [<HKLM>\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ShellIconOverlayIdentifiers\ServerShellIcon] '' = '{D8956119-6E66-43BD-AAA5-231F94859EE6}'.
Thus, the process explorer.exe will load the trojan the next time it restarts.
Main functionality
The trojan starts performing the main functions either by calling the exported function DllUnregisterServerA, or by loading the process explorer.exe. The difference is that when loading by the process explorer.exe, the trojan creates a FEca72d-abc-efef mutex to prevent another copy from running simultaneously.
Next, it reads its configuration from the [HKCU\\Software\\Microsoft\\Keyboard\\Set] 'HPConf’ registry key. If the specified key does not exist or the configuration stored in the registry does not match the hardcoded configuration, it uses the hardcoded configuration and writes it to the registry.
The configuration in the registry and in the trojan’s body is stored in encrypted form: the RC4 algorithm is used for encryption. The encryption key is hardcoded in the trojan body:
13 36 CF 83 2E CC 79 DF 2E AB 79 64
Decryption function:
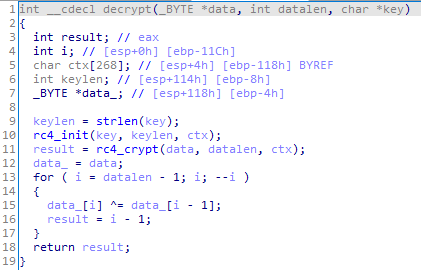
The decrypted configuration has the following structure:
struct st_config
{
_DWORD compname_sum;
wchar_t compname[16];
wchar_t cnc_addr1[64];
wchar_t cnc_addr2[64];
wchar_t cnc_addr3[64];
_WORD cnc_port1;
_WORD cnc_port2;
_DWORD interval;
wchar_t sleep_time[64];
wchar_t fallback_url[128];
};
In the hardcoded configuration, the fields compname_sum and compname have null values. As the trojan decrypts it, it assigns values to these fields, then encrypts the already updated configuration and writes it to the registry. compname_sum is calculated based on the computer name:
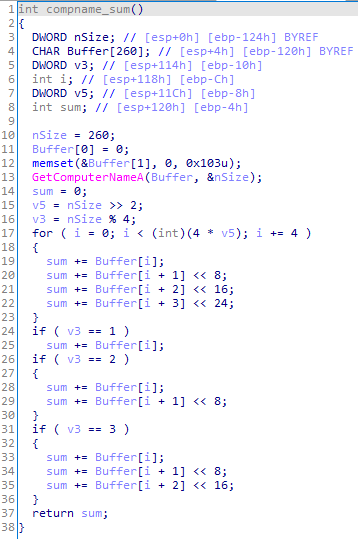
Next, the trojan loads the available plug-ins. To do so, it checks whether the %APPDATA%\\Microsoft\\Media Player folder is present. If it exists, the trojan searches for libraries with two exported functions—GetValue and PluginEntryPoint. For each located library, PluginEntryPoint, and then GetValue are called sequentially. The second function returns the handle of the thread that the trojan is waiting for to complete. After the thread is terminated, the library file is unloaded from the process and deleted.
The sleep_time configuration parameter can contain two dates (year, month, day, hour, and minute) that define the time period when the trojan does not communicate with the C&C server. If the current date and time do not fall within this interval or this parameter is not set, the trojan communicates with the C&C server.
Communication with the C&C server
The trojan configuration can contain up to two C&C server’s addresses. Each server has a specified domain and port. The configuration can also specify the URL to which the trojan sends requests to get the control domain address—fallback_url.
All requests to the C&C server contain the bot ID:
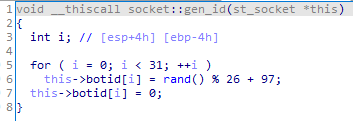
The trojan can send two types of requests:
- A POST request with URI /result?hl=en&meta=<botid>, where botid is the bot ID. The request data is encrypted using the same algorithm as the configuration. The request data is encrypted using the same algorithm as the configuration.
- A GET request with URI /search?hl=en&q=<data>&meta=<botid>, where <span class=”string”>botid is the bot ID, and <span class=”string”>data is the request data encrypted in the same way as the configuration, and then encoded in Base64 and urlencode.
A POST request is only used to send a file from an infected computer to the C&C server if the size of the data being sent exceeds 528 bytes.
The requests use the User-Agent string: Mozilla/4.0 (compatible; MSIE 6.0; Win32).
To check the C&C server’s operability, the trojan sends the st_pkt_hello packet:
struct st_pkt_hello
{
_DWORD rnd;
_DWORD cmdid; // 0x10001000
_BYTE gap[36]; // 0x00
};
where rnd is a random number. If the server responds to this request, the trojan uses this server for further work. If none of the servers specified in the configuration work, the trojan sends a Get request (just like that, not GET) to the specified URL. In response, it expects to obtain the C&C server’s address, encrypted according to the same algorithm as the trojan configuration. The address obtained in this way is then checked for operability in the same way—using the st_pkt_hello packet.
When the trojan finds the C&C server, it starts periodically requesting commands. The packet for the command request is the following:
struct st_pkt_req_cmd
{
_DWORD rnd;
_DWORD cmdid; // 0x10001001
_DWORD compname_sum;
char compname[16];
_BYTE gap[16]; // 0x00
};
where rnd is a random number, compname_sum is the number derived from the computer’s name, and compname is the computer’s name.
If the server responded with the *NONE* string, the trojan ignores the "silent" time specified in the configuration and repeats the request. If the received response is different from *NONE*, the trojan saves this data to the %APPDATA%\\jbl file. This file is then decrypted (using the same algorithm as the configuration) and divided into commands. The trojan determines the command to execute based on its first three characters:
opcode = cmdbuf[2] ^ (cmdbuf[1] * cmdbuf[0]);
Commands list
| Command id | cmd | Description |
|---|---|---|
| 0x2718 | del | To delete a file |
| 0x28D7 | get | To send the current configuration to the server |
| 0x2A43 | cmd | To run the command in the command shell and send the result to the server |
| 0x2B2B | dow | To send a specified file to the server |
| 0x2C89 | sde | To change the time interval for connection to the server |
| 0x2C97 | rem | Self-deletion |
| 0x2D7E | wai | To idle for a specified period of time |
| 0x2EB5 | loa | To launch the trojans plug-in |
| 0x2F3D | exe | To open a file |
| 0x30E1 | sle | To set the inactivity period for the trojan |
| 0x322A | unl | To unload a plug-in and delete it from the disk |
| 0x3353 | upc | To update the configuration |
| 0x3354 | upd | To request and install malicious module updates |
| 0x335C | upl | To get a file from the server and save it to the specified path |