SHA1:
- de74dd60ba3448b072f03ad80001f6a903f60b60
An encryption Trojan that infects devices run by Microsoft Windows. The preventive protection of Dr.Web Anti-virus detects it as DPH:Trojan.Encoder.9.
Once launched, the Trojan checks the user’s location based on the IP address using the 2ip.ru service. Cybercriminals designed the malicious program so that it is not supposed to encrypt files if the device is located in Russia, Belarus and Kazakhstan, or the CultureInfo object that provides information on language and regional parameters has a Russian locale identifier. However, the encoder encrypts all files regardless of the IP address’s geographical location due to the code error.
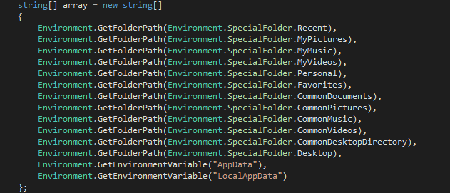
The Trojan installs itself to the autorun using Windows Task Manager and encrypts the content of the following folders:
It encrypts files using the AES-256-CBC algorithms with the same key that is stored in the Trojan’s body. It adds the “.tron” extension to the encrypted files.
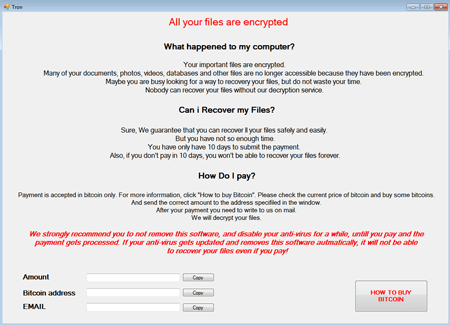
Files that exceed 30,000,000 bytes (about 28.6 MB) are not encrypted. Once the encryption is over, the “123” value is written into the %ProgramData%\\trig file. The Trojan then sends a request to the iplogger website. The website address is hardcoded into the program’s body. The malicious program then displays a window with ransom demands.
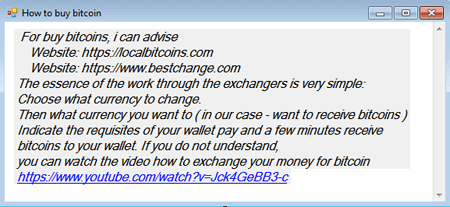
Once the HOW TO BUY BITCOIN button is clicked, the Trojan displays a window with instructions on how to buy the Bitcoin cryptocurrency:
The size of the ransom that cybercriminals demand differs from 0.007305 to 0.04 Btc.
In most cases, decrypting files corrupted by the encoder is impossible due to the code error.