- dec7aec692fed8473f0fc3cab1b10726bf9ee107
- 7c7536ed7a5ff60021398240c0799512fb8c52a4
- 228963460817b4aaac27e2fcdfc121a20571b099 (detected as Android.SmsBot.472.origin)
An Android Trojan that serves the purpose of stealing money from mobile devices' users. It can be disguised as a harmless application, for example, as an official banking application or a voting program.
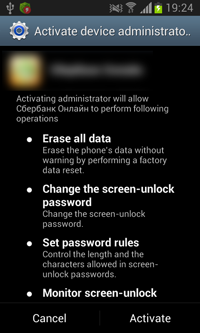
Once the malicious program is installed and run, the Trojan makes an attempt to acquire administrator privileges prompting the user again and again to give their consent.
The Trojan scans the user's contact list sending to all numbers SMS messages that look as follows: Hi! Vote for me http://******konkurs.ru/ (“Привет, проголосуй за меня http://******konkurs.ru/”). The link from such a message leads to a fraudulent website supposedly related to some photo contest. From this website, a modification of Android.BankBot.80.origin detected by Dr.Web as Android.SmsBot.472.origin gets downloaded to the victim's device. Moreover, depending on the operating system of the device, the website offers owners of smartphones and tablets to install a special program for voting.
While sending spam messages, the Trojan connects to the command and control server at http://****bora.com/api/?id=3 forwarding it information about the infected Android device. The information includes the following data:
- method=install — request type;
- &id=FKLKJDFSWXXXXXXXXXXXXXXX — infected device ID, where FKLKJDFSW indicates the parameter from the Trojan's body and XXXXXXXXXXXXXXX indicates IMEI;
- &operator= — mobile network operator;
- &model= — model name;
- &os= — OS version;
- &phone= — phone number;
- &imei= — IMEI;
- &version= — Trojan version;
- &country= — system language.
After that, Android.BankBot.80.origin waits for further commands from cybercriminals periodically connecting to the remote node to get new instructions. The Trojan can execute the following commands:
- call_number—forward calls to a specified number;
- sms_grab—set a time interval for concealing incoming SMS messages (if a message is received during this interval, the Trojan blocks a corresponding system prompt deleting the message);
- sms_send—send an SMS message;
- ussd—send a USSD query;
- delivery—send an SMS message with specific text to all numbers from the contact list;
- new_url—set a new command and control server address;
- install_true—save the inst flag changes to the configuration file (AppPrefs).
When the user receives a message, the Trojan forwards information regarding that message to the command and control server. If by using the sms_grab command a time interval for concealing incoming SMS messages has been set, the Trojan blocks the corresponding system prompt deleting the message.
If the delivery command is executed, all incoming calls will be forwarded to +79009999999:
callforward(this.context, "*21*+79009999999#"),As a result, the victim will not be able to receive incoming calls.
This malicious program can stealthily steal money from mobile accounts, bank accounts, and payment system accounts.