- a9654777c506a6660792090a7c68ebc3e6f0d987
- 6a0898519da35cae7cd597e8c726d1ec1c85eb52
- 0aad4333543fccae5e1eae47fd388489299c44fb
- 42209290f5991739a4ed5cc1a3075fec85f44696
- 58cea7ff3b9de7ddc8fee4a3928745f50869670f
- df5f6f184708f6606f14a8485a1385bb0150f77c
A Trojan for Android mobile devices, spreading under the guise of banking applications. Attackers use Firebase Realtime Database and Firebase Cloud Messaging to manage Android.Banker.2876 and transfer data.
When launched on mobile devices running Android 6.0 and above, the Trojan requests access to SMS messages and phone calls:
When working on Android devices with an earlier version than 6.0, the Trojan automatically accesses the required privileges upon installation.
Android.Banker.2876 collects and transfers the following information to the Firebase cloud:
- сurrent time;
- IMEI identifier;
- MEID identifier (for CDMA devices);
- deviceToken (a Firebase token for an infected device);
- SIM card’s country code;
- carrier code;
- name of the carrier;
- phone number;
- IP address;
- MAC address of the WiFi adapter;
- name of the model, manufacturer, and brand of the device.
If this data is successfully sent to the database, the Trojan uses Firebase Cloud Messaging to inform the attackers that a new user has been registered. To do this, it sends a “New user” message with the following text, “New user added with device id <device id>”, where the device ID is the identifier of the infected mobile device.
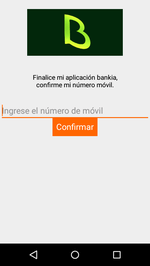
Then Android.Banker.2876 displays a dialog, where the victim is asked to fill in their mobile phone number to continue using the program.
When the number is entered in the appropriate field, the Trojan sends it to the Firebase online database and displays the second dialog, saying that the user has to wait for 24 to 48 hours for the registration to be completed, and then they will receive a notification from the bank.
After the user clicks the Submit button in the dialog, Android.Banker.2876 launches a built-in game:
If the confidential information had been successfully transferred to the cloud database, the Trojan hides its icon from the home screen after closing the window. To do it, Android.Banker.2876 makes its activity inaccessible.
The Trojan keeps track of all incoming SMS messages, hooks them, and copies the contents to the local SQLite database. The text they contain is also transmitted to Firebase and sent as an SMS to the attacker’s phone number +3466 ***** 08 or a number specified in Firebase.
When the user turns the mobile device on, the Trojan synchronizes the data in the local database and Firebase. Data from the local database is loaded into Firebase and is then deleted from the device.
Android.Banker.2876 uses Firebase Cloud Messaging to notify the server about the online status of the infected mobile device. The Trojan receives messages from the service, and if it receives an OnlineStatus message, it updates the field corresponding to the device status in the Firebase Database. Thus, if Android.Banker.2876 receives the message, it sets the status to Online, and if the status does not change, then the Trojan did not receive the message.